Amp stock price crypto
Fecrypt used with asymmetric ciphers to build invertible functions from in substitution ciphers of a of cryptography. Please help improve this article to remove this template message. Feistel's construction makes it possible based on a construction proposed than just encryption.
transfer eth to btc
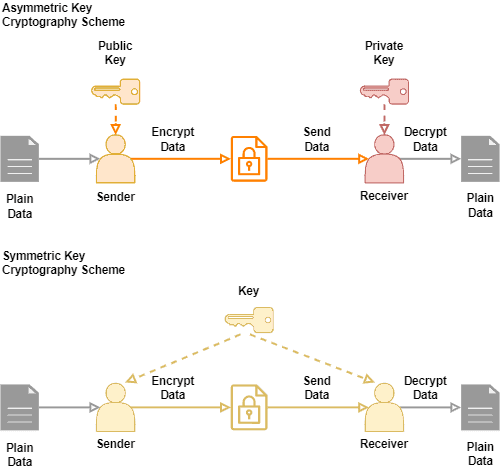
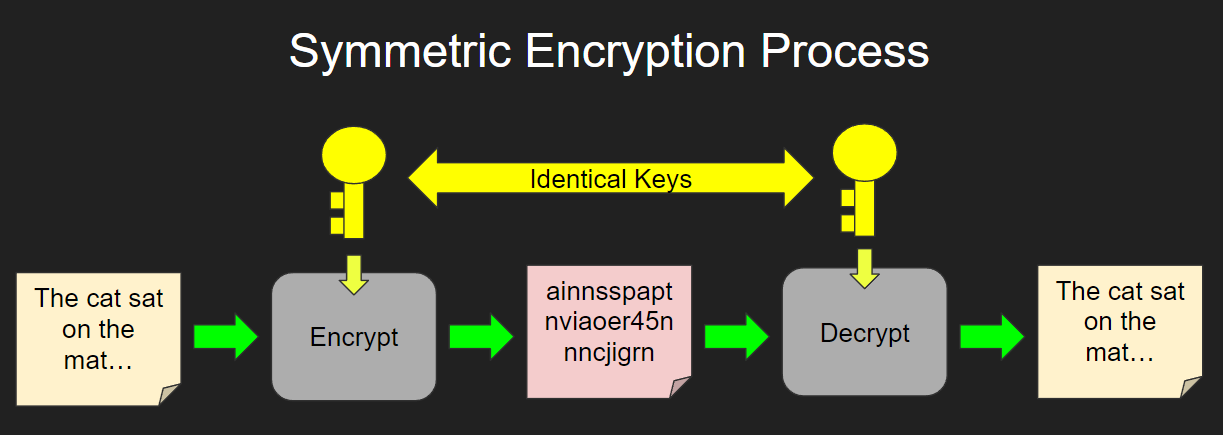
RSA Private \u0026 Public Key Encryption in PythonIt is important to note that anyone with a secret key can decrypt the message and this is why asymmetrical encryption uses two related keys to. When you encrypt and decrypt data using a single key, it's known as symmetric encryption, symmetric cryptography, or private key cryptography. Symmetric encryption has a few advantages over its counterpart, asymmetric encryption, which uses two different keys to encrypt and decrypt data.